| Last updated 29 Aug 2016 |
Skill and Focus Matrix
This Schneier on Security blog (HTTPS Direct) is about how you can characterize attackers using two axes: one for skill and the other for focus. The points in the above blog provides the basis of the four quadrants of the following diagram: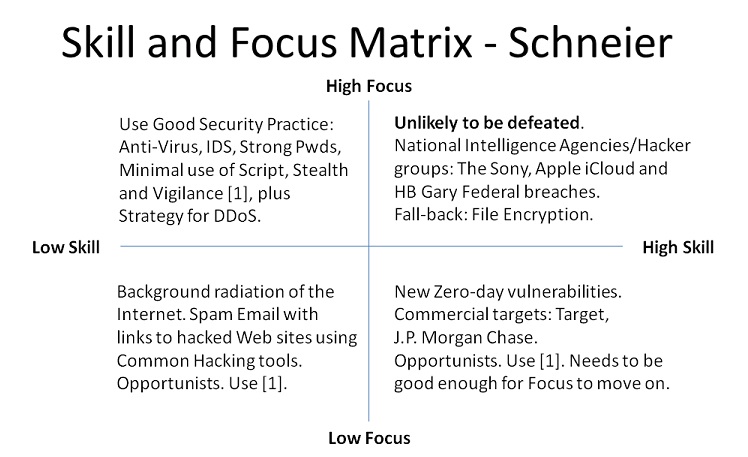
Note: The only quadrant that Schneier doesn't cover is the low skill, high focus one. This is like targetting a range of IP Addresses to see what is there and might appear to be a Distributed Denial of Service (DDoS) attack. In this quadrant is the definition of what will likely defeat such an attack and labelled as [1]. If you can, stealth your connection to the Internet. This means that scans of your IP Address will reveal little, if any, information about what resides at your Address. To test your IP Address, use something like Gibson Research Corporation (GRC) Shields Up (HTTPS Direct).
In the high skill, high focus case one fall-back is to use file encryption to buy time. Any PC that is breached is likely to provide passwords to decrypt files, but if other PC's share encrypted files (for example on file servers), those files are reasonably secure because each PC will need to be breached to get relevant passwords. This amounts to a form of containerization and means more work for the attacker (either trying to get passwords, or using a brute force approach to cracking the encryption). If files are in plain text an attacker can breach one PC and may have access to lots of shared files. In this scenario, employees need to be vigilant for unusual behaviour in Email messages requesting files (odd times outside of normal working hours, many requests).
Using containers is associated with the strategy of restricting access to resources, such as files, according to least privilege. In Microsoft Windows encironments, traditionally (in a Domain scenario), people have been assigned to global groups specifying privilege levels and then these global groups are applied to Domain local groups which represent things like resources (such as printers) administered by the Domain. There are also universal groups, see this Microsoft Technet blog (HTTPS Direct).
For example: 5 users need access to a Domain printer. Assign them to a global group and then add that group to the Domain local group. If those same users require access to another printer, just assign the global group to that printer's Domain local group (otherwise you have to assign each of those users to the Domain local group). If the number of users in in the hundreds, you can see that global groups assigned to Domain local groups is administratively effective. However, to support resource containers, each PC needs its own container, in order to mitigate an internal breach which would likely make all the resource container controls obsolete. This is usually done with a combination of whole disk encryption and a policy (supported by at least one Standard Operating Procedure [SOP]) requiring that when a person is away from their PC, they at least lock the PC so that the password is required to unlock it (this assumes Windows 2000 and later).
AllIncontext Limited is registered in England, No
04624520.
Registered office address: 12-14 High Street, Petersfield, Hampshire, GU32 3JG.



